Software-Defined Networking (SDN) Solution
SDN Solution helps to increase business agility for our clients by providing self-service access.
Last updated on
About
One of the main goals of the SDN Service was to increase business agility for our clients. Business agility is enhanced by providing self-service access in the areas of security policy management, load-balancing configuration as well as increased visibility into configuration and log data.
Providing self-service capabilities in the hosting environment is predicated on 2 things:
- The ability to enforce a Zero-Trust/Least Privilege security model
- Support for multi-tenancy that presents each client with a view into their specific infrastructure and theirs alone. The SDN solution enforces Zero-Trust/Least Privilege by way of the guardrail policies enforced by NSX. Multi-tenancy is achieved by leveraging the capabilities of ReSTNSX
Self-service capabilities
- Security policy management for virtual machines
- Load-balancer configuration and management
- Access to log data
- Access to network flow data
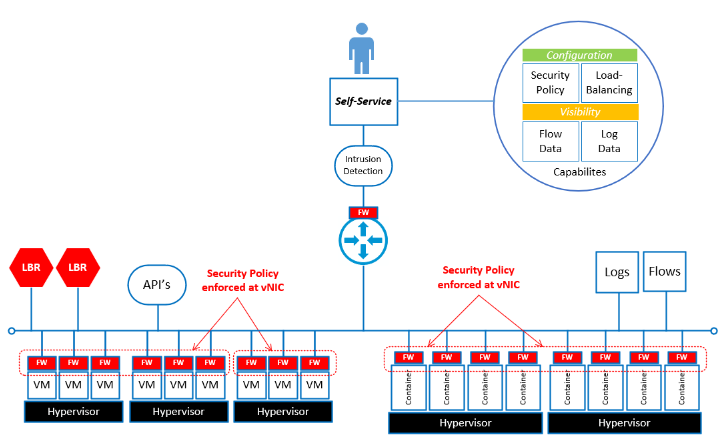
Guardrail policies
The Zero Trust/Least Privilege security model is underpinned by a guardrail policy. The guardrail policy serves as the default policy framework and is enforced at various locations in the SDN. The default policy restricts access to and from data centre resources, the enterprise network and the internet. Having a solid understanding of the guardrail policy will make it easier to work in a Zero Trust environment. The guardrail policies are not self-service and can only be modified by the SDN operations team. Changes to the guardrail policy are exceptions and must be approved by Hosting Technical Stewardship.
Keep in mind:
- When a new tenancy is created a default deny rule is also created (this rule is managed by the tenant)
- To permit access to resources in your tenancy, explicit rules will need to be created
- This applies to resources within the SDN. For example, 2 VM’s within the same security zone will not be able to communicate with each other without creating a specific rule that permits it
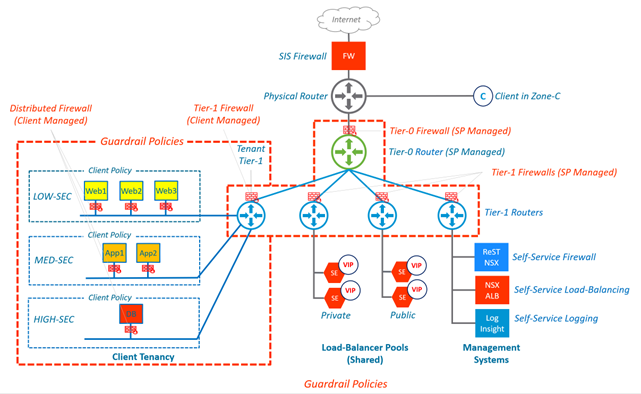
Distributed firewall rules
The Distributed Firewall (DFW) is the primary Zero Trust enforcement point. The Distributed Firewall enforces policy at the vNIC level of each individual Virtual Machine (review diagram). The Guardrail Policy with the Default Tenancy Rules (created during tenant setup) blocks all traffic inbound to the SDN, traffic outbound from the SDN and ALL VM-to-VM communication within the SDN, with one exception. The exception being the Virtual Machines in the SDN are permitted access to the following Enterprise network services listed below.
These exceptions are in place to streamline the deployment of new workloads.
- WINS service
- Authentication services (IDIR, TIDIR, DMZ Active Directory Domains)
- Microsoft KMS services (On-Prem Key Management Service for license Activation)
- DNS services
- NTP service
Perimeter rules
At the perimeter of the SDN the guardrail policy is enforced at the Tier-0 Firewall (review diagram). The policy rules at the perimeter are designed to be open with one exception.
The Perimeter Guardrail Policy can be summarized as:
- SPAN-BC in permitted (Any, Any) access to the SDN Low and Medium Zones
- Zone-A is permitted (Any, Any) access to the SDN Medium and High Security Zones
- Zone-B is permitted (Any, Any) access to the SDN Low, Medium, High Security Zones
- Zone-C is permitted (Any, Any) access to the SDN Low and Medium Security Zones
- Zone-DMZ is permitted (Any, Any) access to the SDN Low and Medium Security Zones
- SDN Low Data Classification Segments are permitted (Any, Any) to Zone DMZ and Medium Data Centre Security Zones
- SDN Medium Data Classification Segments are permitted (Any, Any) to Zone B and Zone A Data Centre Security Zones
- SDN High Data Classification Segments are permitted (Any, Any) to Zone B and Zone A Data Centre Security Zones
- Access to Enterprise shared services is allowed [Ingress and Egress] for services that support the run and deployment of Operating systems (Active Directory, DNS, NTP, Licensing)
Multi-tenancy
In a multi-tenant environment, all or a part of a common infrastructure is shared by multiple clients or “tenants”. Although the infrastructure is shared each tenant is only able to view their specific object and configurations. Multi-tenancy in the SDN environment is centred around Security Policy and is typically at the division level. A tenant can be given the ability to create and manage their divisions security policy, firewall rules, firewall objects, security tags and security groups. Without a multi-tenant capable solution, all clients would have visibility and control over another client’s infrastructure and configuration.
Each tenancy has a low-security, med-security and high-security zone/segment. These new zones mimic the function of our classic data centre zoning model. Each of these zones are associated with a network segment and subnet. This is a Zero Trust environment. Each tenant’s space is protected by guardrail policies which limits their VMs ability to communicate outside of the SDN environment. The default guardrail policies permit VMs to connect to the network services noted above. The SDN uses RFC 1918 private IP address space within the security zones, for applications servicing external clients (such as Internet Facing Applications, where a Public IP will be used to front end your application.)
Networking
As outlined in the strategic objectives, one of the main goals of the SDN service is to increase business agility for our clients. Business agility is enhanced by providing self-service access in the areas of security policy management, load-balancing configuration as well as increased visibility into configuration and log data.
Self-service capabilities
- Security policy management for VM’s – Configuration and management
- Load-balancing – Configuration and management
- Log data analysis
- Network flow data analysis
